Are you at risk of the data pirates?
 We used to think of viruses as something malicious created for no other reason than to do damage. Most virus attacks were untargeted and caused by bad practice and were reasonably easy to protect against with good working practice, education and a well supported piece of antivirus protection. Unfortunately, viruses and other forms of malware are now a large criminal business making huge amounts of money for organised crime around the world, unfortunately they now often target particular organisations and employees using personalised messages to make you more likely to become infected.
We used to think of viruses as something malicious created for no other reason than to do damage. Most virus attacks were untargeted and caused by bad practice and were reasonably easy to protect against with good working practice, education and a well supported piece of antivirus protection. Unfortunately, viruses and other forms of malware are now a large criminal business making huge amounts of money for organised crime around the world, unfortunately they now often target particular organisations and employees using personalised messages to make you more likely to become infected.
The worrying malicious software is something called “Ransomware”. There are different types of ransomware however they do one of a few things.
- Prevents access to your computer by “locking” it or disabling all logon
- encrypting all your data with a key you do not have
- stop certain applications running
Ransomware will then demand that you pay money to get access to your computer or your files again. There is no guarantee that paying the fine or doing what the ransomware tells you will give access to your PC or files again.
Lock Screen Ransomware
This type of ransomware shows a message full screen on your system 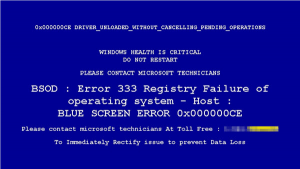 and prevents you doing anything. The message on the screen will claim you have done something illegal on your system and are being fined by the police or government agency, these claims are designed to scare you into paying without telling anybody who can restore your system like your IT support.
and prevents you doing anything. The message on the screen will claim you have done something illegal on your system and are being fined by the police or government agency, these claims are designed to scare you into paying without telling anybody who can restore your system like your IT support.
The newer type has taken on a more “helpful” tone and puts a horrible computer error in full screen making you think the computer has a problem and providing a phone number to tech support, this is often a premium number or they will ask for payment, again there is no certainty they will help. You can only be sure they will take money and possibly if you give bank or card details, more than you think.
Encryption ransomware
This is far more concerning fo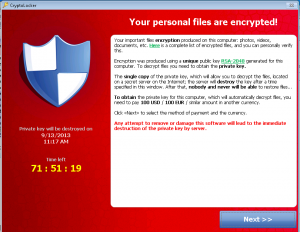 r business because it does not just affect the computer the user is on but also all the data they have access to, the software goes through all the data and encrypts it with a key and then demands money for access to the decryption key. If your company allows all users access to all data, then a single user being infected with this type of Ransomware could remove access to all data on the network. This is also a concern for OneDrive and SharePoint because although you should be able to recover versions of your data this will only be one file at a time which is time consuming. Microsoft may be able to restore a version of your entire SharePoint tenant but this will potentially lose days of work and is not guaranteed.
r business because it does not just affect the computer the user is on but also all the data they have access to, the software goes through all the data and encrypts it with a key and then demands money for access to the decryption key. If your company allows all users access to all data, then a single user being infected with this type of Ransomware could remove access to all data on the network. This is also a concern for OneDrive and SharePoint because although you should be able to recover versions of your data this will only be one file at a time which is time consuming. Microsoft may be able to restore a version of your entire SharePoint tenant but this will potentially lose days of work and is not guaranteed.
How do you get infected?
There are many ways to get infected, the ransomware itself is most commonly delivered from a malicious website allowing the owner of the site to keep the ransomware updates so antivirus cannot spot it.
cannot spot it.
- Malicious website itself found when browsing – often the led to by a series of clicks through websites which offer pictures of celebrities or money making schemes or ways to improve parts of your anatomy
- emails – this is still a favourite, to send you an email with a link with a nice title and potential saving, or copy of your invoice or similar but the site is fake and is actually there to infect your PC
- Attachments – Word, Excel documents can contain executable code (macros) which can infect you, ZIP files are also a favourite as often you download and save these files and inside they contain executable files which have the same icon as a document type you expect.
- Hacked websites – yes sometimes people get their website hacked so what would be a trusted site actually contains code which will infect you. this is a subtle and effective way these criminals use to get their claws into your systems
- Other malware – if you are already infected with something else or deliberately install something like a key generator or application “patch” to get around licencing, these are often vectors other malware uses to get into your system.
- Installed with software – The criminals know you want to convert that document for “free” so they will offer software or websites which do it, however be careful sometimes what seems too good to be true, is.
So what do we do?
As with most malware, the ideal is to not become infected, help in many ways
- Good and up to date antivirus – CenCom supply Bitdefender based antivirus which for their customers they monitor to ensure you are up to date
- Web protection – no matter how good your antivirus is some sites or online services are malicious or illegal, CenCom web protection will minimise the risk of you or your colleagues visiting and accessing dangerous content.
- Patch Updates – Not just windows, but browsers and applications like Adobe Reader, or iTunes all have vulnerabilities which can be exploited to damage or take control of your systems, patching them up to date minimises this risk and CenCom Solutions Patch Management will do this for you.
- Don’t run with local admin rights, if you do not have the ability to install software you are less likely to cause problems, CenCom recommend you use your computer with a low privilege account and that either you use our helpdesk to install software or you have someone responsible internally who can enter an admin password when required.
- Make sure your important data is backed up, CenCom can help in planning this including backup of your server data both locally and online, backup of your local computers to the cloud and we can backup your SharePoint and OneDrive libraries too.
If the worst happens and you become infected, then the “surface area” of what is affected should be kept to a minimum. This is good practice anyway
- Only sync the SharePoint sites you need on a day to day basis, any which you only need occasionally use online.
- If you carry local data which is not stored on servers get a local backup (not an external or second drive which is always connected because this would be affected too) – CenCom Solutions can backup your workstation online from £10 per month
- Only have access to the server data you need. If all your company data is in folders and users have access to all of it, then all of it is at risk from any user. If you split your data into departments and users only have data they need, your risk is largely reduced.
If all else fails and you have a ransomware infection
- STOP – all users should stop everything. The problem needs to be assessed before more data is lost
- Contact CenCom on 01892614040 – We will then help you figure out the best way forward.
- Backups – this may be your only option, so CenCom will need access to them but do not connect them until requested to do so because we do not want to infect them.